Dashboard
From the Dashboard page, view details about your networks so you can prioritize and address urgent issues.
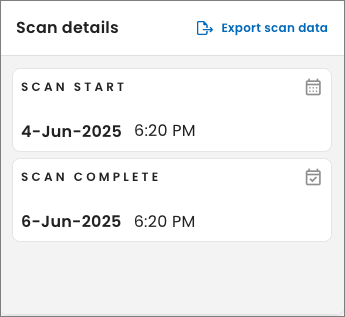
Scan details
Under Scan details, view the dates we started and completed the selected scan. You can choose which completed scan to view from the Scan date field in the header of the SixMap app. The frequency of the scan dates corresponds to the schedule your organization and SixMap account representative determined during onboarding.
You can also select the Export scan data link to download a .tar.gz archive (tarball) of data from your current scan to your browser’s Downloads folder. Use the comma-separated values (CSV) files in the archive to analyze data, create reports, or integrate with other systems.
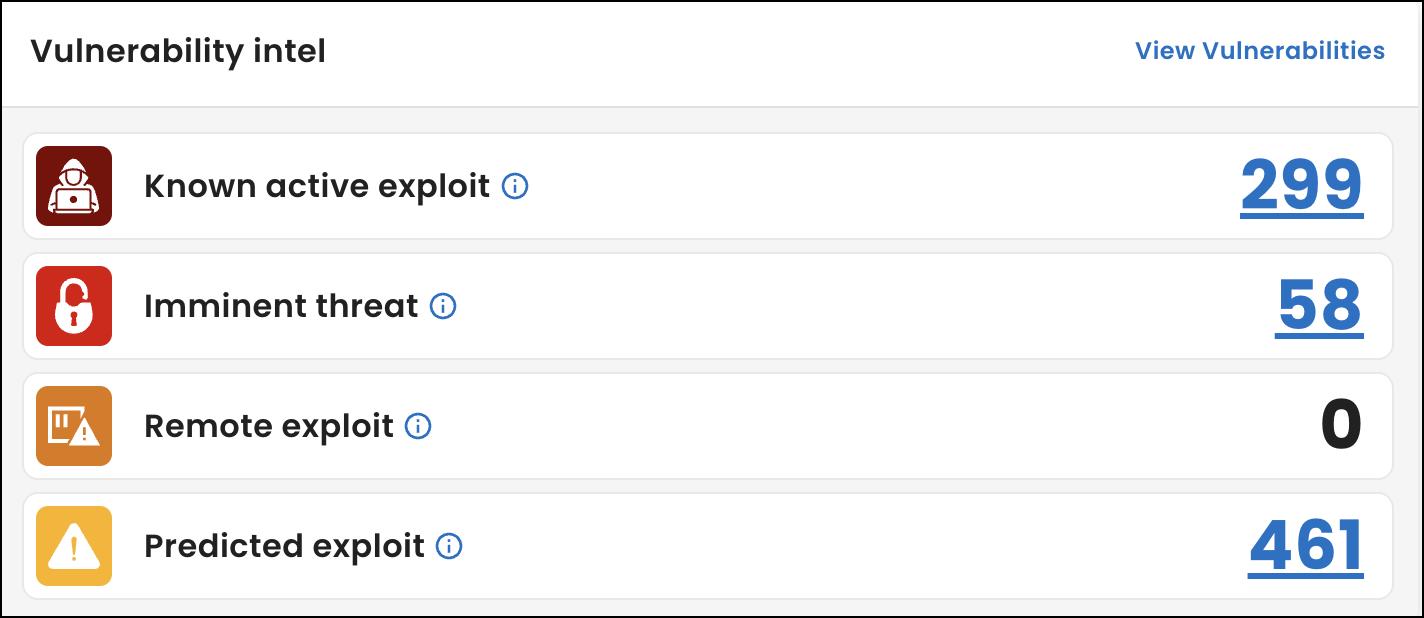
Vulnerability intel
Under Vulnerability intel, view how many vulnerability instances have the highest threats to your organization based on tags. A tag is a label we add to scan data to help you quickly identify areas within your networks that might require attention. To assign vulnerability tags, we use industry measures such as the Known Exploited Vulnerabilities (KEV) catalog, Exploit Prediction Scoring System (EPSS), and the Common Vulnerability Scoring System (CVSS).
An instance is a vulnerability related to a software service, product, and version for an IP address running the service on a specific port. If an IP address runs the service on multiple ports, we count each port as an instance.
-
Known active exploit: Listed in the KEV catalog. The catalog lists vulnerabilities your organization should immediately address because they meet specific criteria, including being exploited by threat actors and causing damages to victims or on highly available and highly distributed systems like Microsoft Internet Information Services or a Remote Authentication Dial-In User Service (RADIUS) server.
-
Predicted exploit: Has an EPSS score greater than 0. The EPSS score, ranging from 0 to 1 (0 to 100% exploitation chances), estimates the probability that a threat actor will exploit a vulnerability within the next 30 days.
-
Imminent threat: Has an EPSS score greater than .9.
-
Remote exploit: Is remotely exploitable according to the metrics used to determine its CVSS score. The CVSS assesses the severity of vulnerabilities and assigns scores to them using a formula that measures the ease and impact of exploitation.
For more information about the industry measures we reference, see CVE program.
To view all of the vulnerabilities in your networks, select View Vulnerabilities.
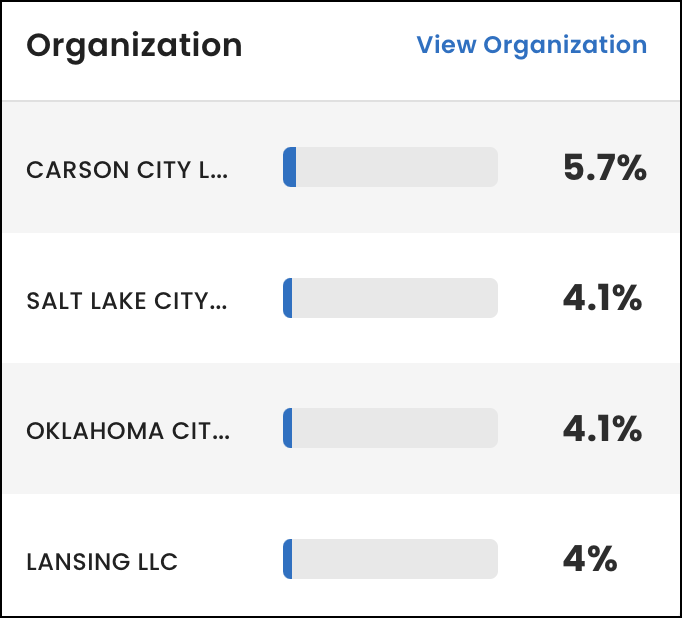
Organization
Under Organization, view the four descendant organizations from your hierarchy with the most IP addresses.
Next to each organization, view the percentage of IP addresses associated with it. To calculate each percentage, we count the number of IP addresses in networks associated with the organization. Then, we divide the number by the total number of IP addresses listed in the IP addresses table.
To view all of the descendant organizations in your hierarchy, select View Organization.
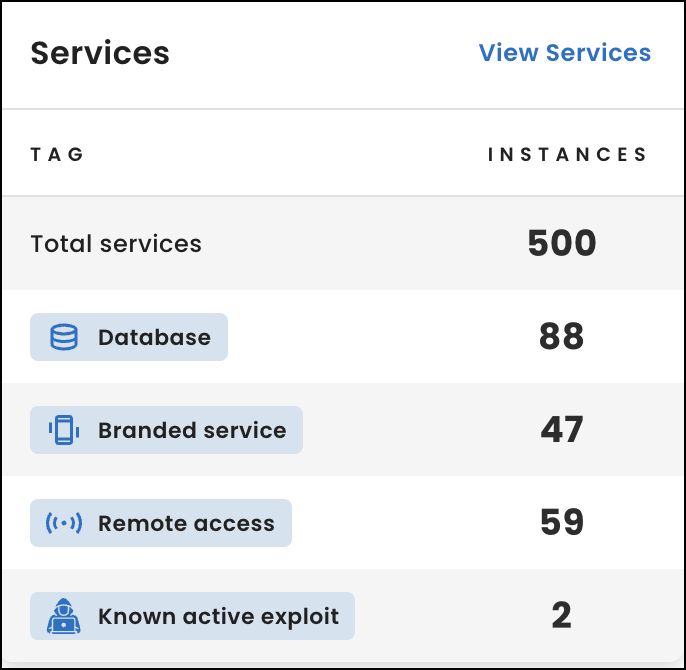
Services
Under Services, view how many service instances are running in your networks. An instance is a service, product, and version combination on an open port. If there are multiple instances of a combination running on multiple ports, we count each port as an instance.
Below the total, view how many service instances are potentially vulnerable based on tags. For details about each tag, see Service tags.
To view all of the services in your networks, select View Services.
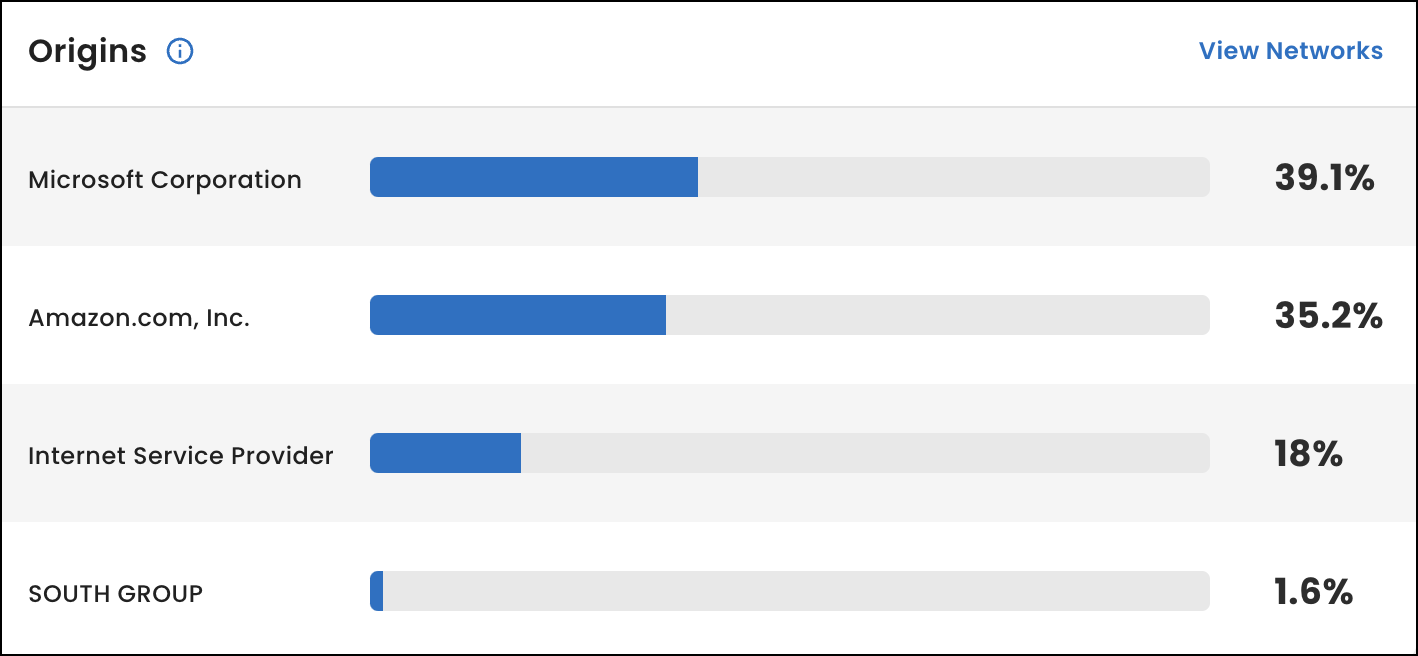
Origins
Under Origins, view the top four organizations that hold the rights to your IP addresses and are responsible for their connectivity to the internet, such as cloud hosting providers, third-party vendors, or your organization if you self-host your services.
Next to each origin, view the percentage of IP addresses it holds. To calculate the percentage, we use the number of IP addresses listed in the Networks table associated with the origin and divide it by the total number of IP addresses listed in the IP addresses table.
To view all of the origins for your organization, select View Networks.
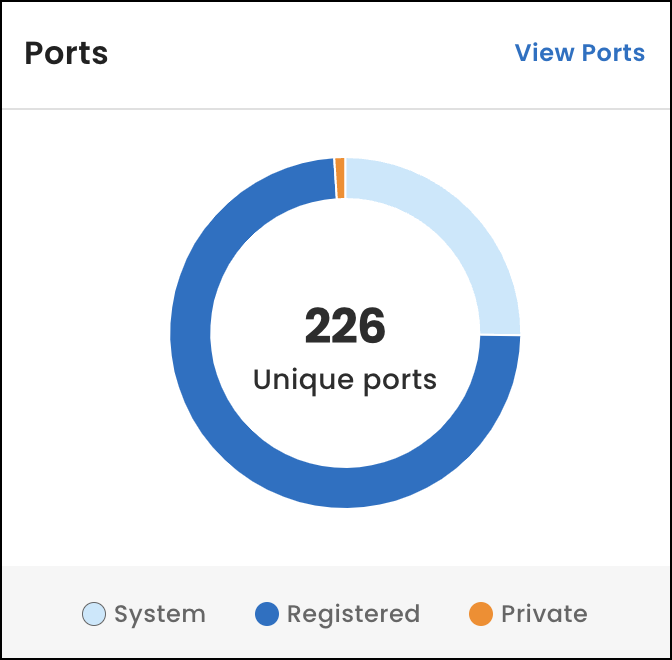
Ports
Under Ports, view the total number of unique ports running services on active IP addresses in your networks. You can also view how many port instances are in the system (well-known), registered, and private ranges. To view each total, hover over the graph.
To view all of the ports in your networks, select View Ports.