Release notes
Learn about the latest changes and updates to the SixMap app.
22 July 2025
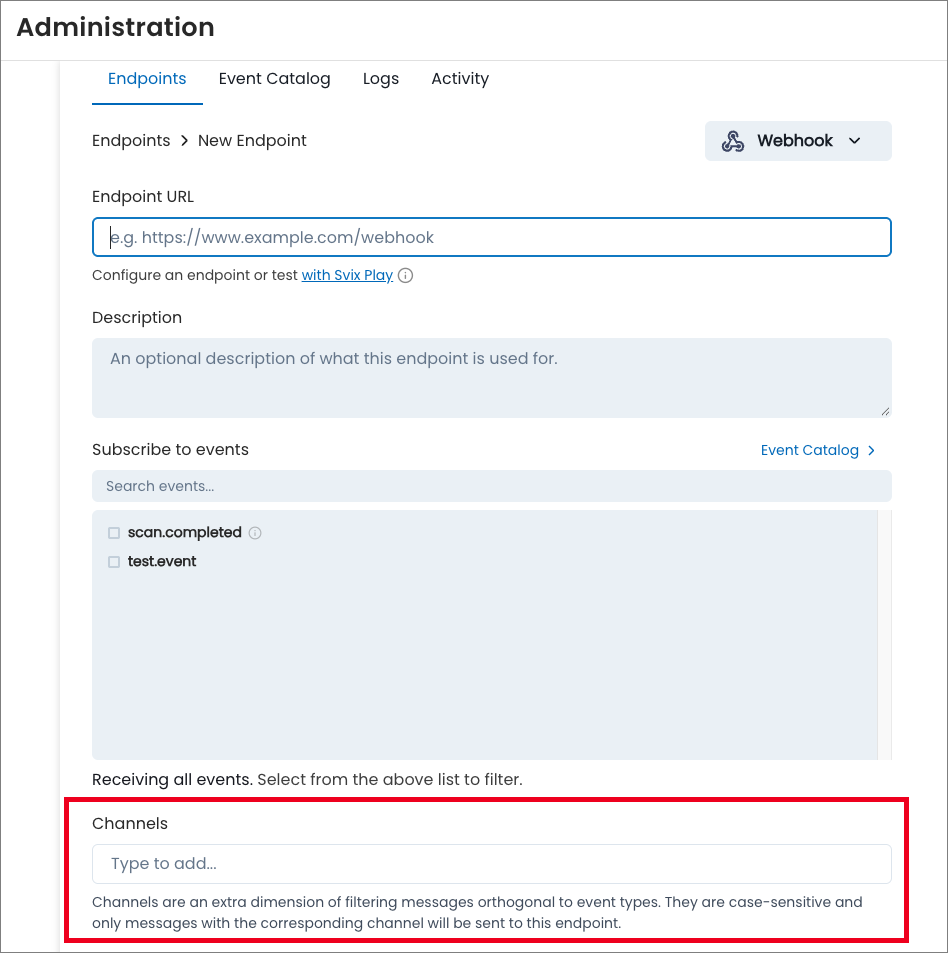
Route webhook event messages by account
To give admins greater flexibility in implementing SixMap webhook endpoint URLs, we introduced channels. Channels are tags you assign to your webhook endpoint URLs, enabling you to specify which endpoint URLs receive event messages.
Currently, we only support channel routing by account for the scan.completed event type. If your organization has multiple accounts, you can configure webhook endpoint URLs in SixMap for each account. As you add or edit the URLs, enter the relevant account slugs in the Channels field. When SixMap sends an event message associated with a particular account, we only deliver it to the webhook endpoint URLs configured to listen for that account's specific slug. Endpoint URLs without channels receive all event messages. For more information, see Webhook endpoints.
You can find an account's slug in the URL of any of the SixMap scan results pages, such as Ports or Services.
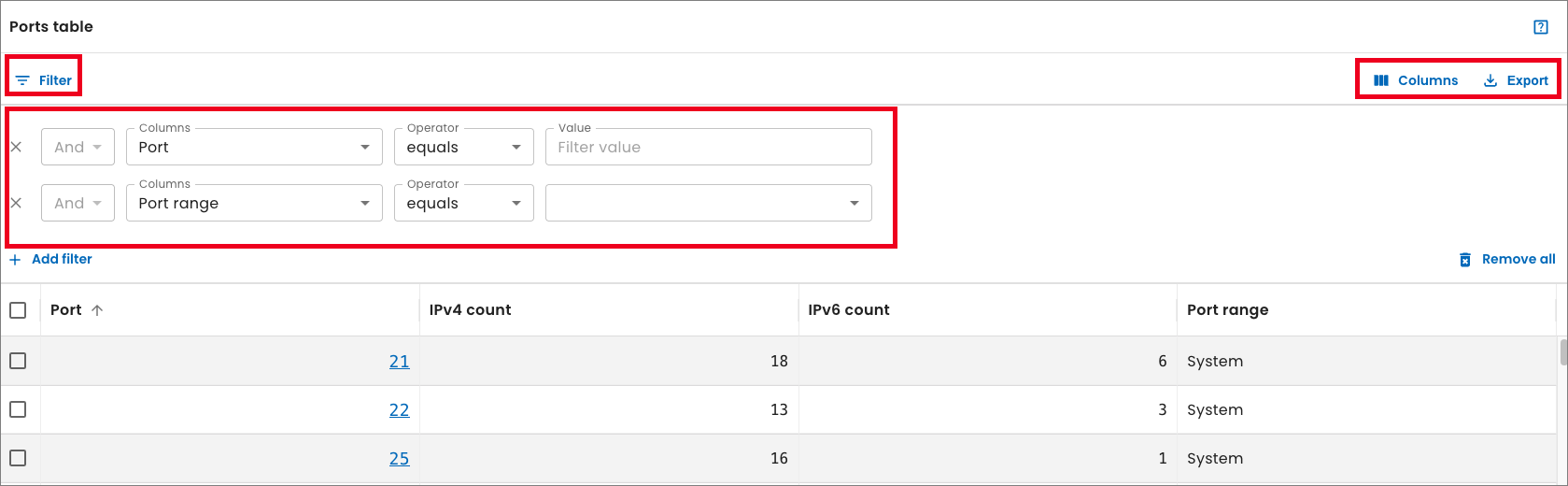
Enhanced table experience
We enhanced the table filtering experience throughout the SixMap app. We repositioned the filter panel to appear directly above each table, making it easier to view changes to the table data as you apply each filter. This improvement addresses the previous challenge where the filter panel obscured the table, requiring you to close the panel to view the results.
We also refined the table toolbar by removing the Density option, and repositioned the Columns and Export options to the right side. This change streamlines the toolbar, providing a cleaner and more intuitive layout for managing your table views and data exports.
View CPE details in API responses
The responses for the Get service details and Get services endpoints in the SixMap API now include the serviceCpe field. The field provides the Common Platform Enumeration (CPE) details for the returned data including the vendor, product, and version information.
08 July 2025
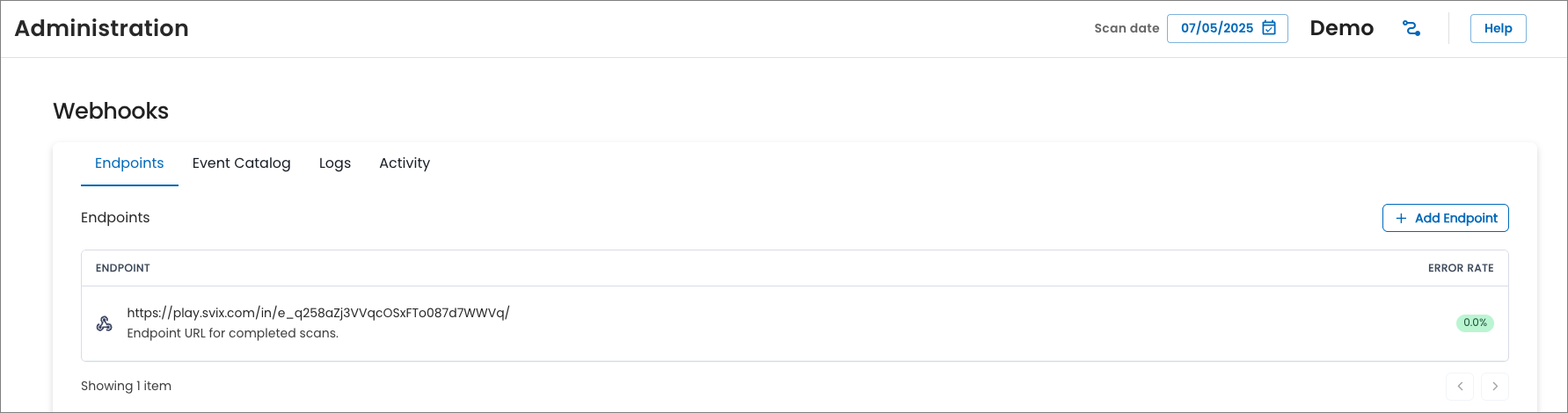
Implement webhooks
To help you integrate security insights directly into your existing operational workflows and tools, SixMap now offers webhooks. From Administration, Webhooks, admins can configure custom endpoint URLs where SixMap will send event messages.
This feature simplifies the incorporation of SixMap data into your applications and systems, providing a push-based mechanism that requires less complex code than polling our APIs. Instead of your organization needing to check for updates regularly, SixMap proactively pushes relevant security events and asset changes to your chosen endpoints as they happen.
For more information, see Webhooks.
For this initial release, the only available event message type is for scan completion. We'll introduce additional event types in future releases.
24 June 2025
Export scan data output enhancement
We updated the Export scan data feature on the Dashboard page to use the Get scan data API endpoint, which provides output consistent with the data in the SixMap app UI. This change resolves an issue where the previous raw data did not align with the UI's structure and moves the feature out of beta.
For details, refer to the Get scan data API documentation.
13 May 2025
Export API data in CSV format
From the SixMap API, you can now export scan data in a comma-separated values (CSV) format by specifying format=CSV as a query parameter. Previously, the API only supported JSON format responses.
The following endpoints support CSV:
- Get accounts
- Get scans
- Get organization groups
- Get domains
- Get networks for a given scan
- Get port instances
- Get port summaries
- Get service instances
- Get service summaries
- Get vulnerabilities
- Get vulnerability instances
- Get IPs for a given scan
Refer to the API reference documentation for details about the specific CSV structure and available fields for each endpoint.
Get scan data endpoint
To help you easily export all the data from a specific scan, we added the Get scan data endpoint to the SixMap API.
The endpoint returns a tarball of data containing scan results in CSV or JSON format. The files in the tarball include details about domains, IP addresses, networks, organization groups, port instances, ports, service instances, services, vulnerabilities, and vulnerability instances. For details, see Get scan data.
Improved organization structures
Before we perform external scans of your organization’s network, we research your organizational structure. We find the names of the organizations within the hierarchy and identify the names of additional companies, subsidiaries, or other entities in which your organization has a vested interest.
We also identify search terms to help our scan engine find IP registration information. Typically, search terms are variations of the organization and descendant organization names. For example, name variations for the National Example Company could include:
- National Example Company
- National Example Company, Inc
- National Example Company Inc.
- NEC
To simplify how we present your organization's structure, we now combine results for multiple search terms to show fewer organizations and organization groups within your hiearchy.
If necessary, you can submit change requests to update the order of the organizations within your hierarchy. Change requests enable you to work with SixMap to modify the raw information we identified during our initial research and record searches. To submit a request, select Change request from the left navigation of any page in the SixMap app, and enter the information you’d like us to add or remove.
Enhanced data quality
We improved our data collection and processing pipeline for reconnaissance and discovery activities, resulting in more comprehensive findings across your external attack surface.
30 April 2025
Access the SixMap API
The SixMap API is now available, providing programmatic access to your threat exposure management data. Integrate SixMap with your existing systems to retrieve information about your accounts, scans, organizations, domains, networks, ports, services, vulnerabilities, and IP addresses.
For details about authentication, available endpoints, and request parameters, see our API documentation.
Generate API Tokens for secure API access
To use the API, you need to generate API credentials (tokens) from Organization, API tokens, or Profile, Personal API tokens within the SixMap app. The API uses these credentials to verify your identity and authorize your access.
API credentials have two parts: a token ID and a token secret.
- Token ID: The token ID is a publicly shareable identifier for your API credentials. Similar to a username, the API uses it to identify which set of credentials you are using.
- Token secret: The token secret is a confidential key you must keep secure. Similar to a password, the API uses it to authenticate your requests and prove you're authorized to use the token ID.
When generating API credentials, you can create:
- Organization tokens: Admins create and manage organization API credentials for team, project, or organization-wide integrations, to ensure centralized control and consistent access for multiple users.
- Personal tokens: You create and manage personal API credentials for integrations or tasks, such as testing, that don't involve other users.
For details, see API tokens.
15 April 2025
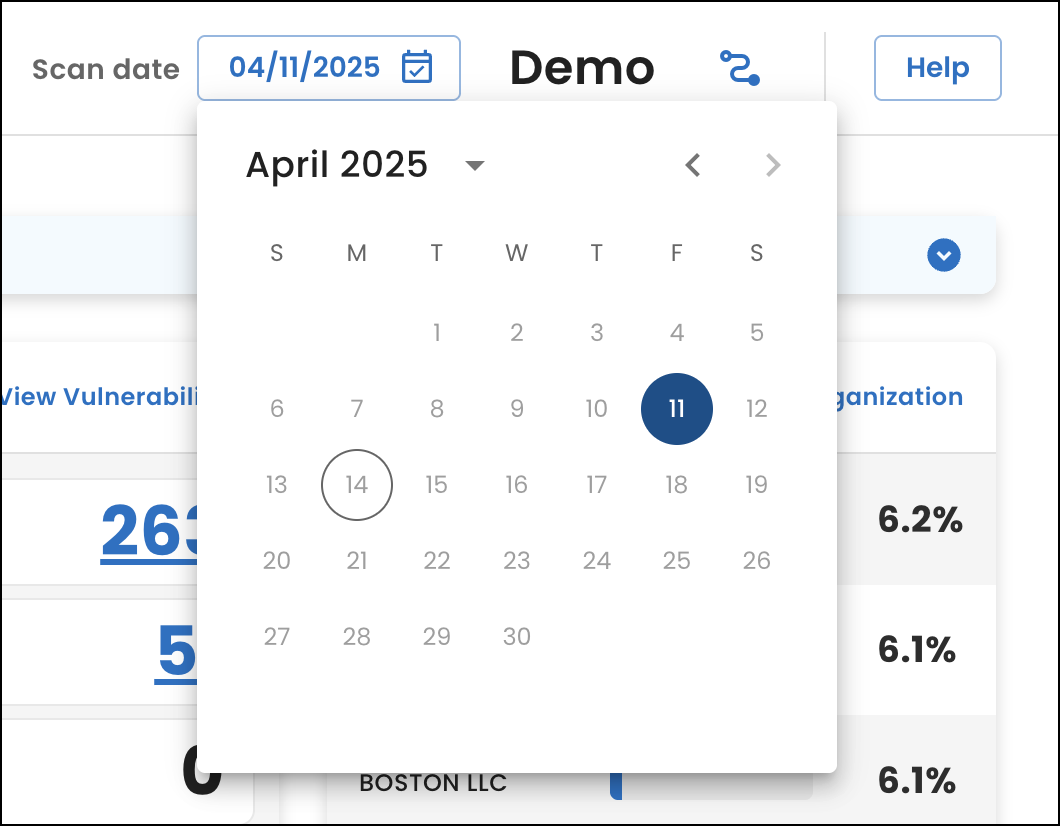
View historical scan data
To help analyze how your organization's security posture has changed over time, we added a new calendar feature to the header of the SixMap app. From the Scan date field, you can now select a date when we completed a scan to view your historical data throughout the app.
You can only select dates that correspond to completed scans.
This update helps you directly compare previous scan results with your current data to identify improvements, regressions, and long-term trends in your attack surface. To compare scans side-by-side, select a scan date in one browser window and then open another window to choose a different date.
View vulnerability intel tags for an IP address
To improve efficiency as you review individual IP addresses, we added the Vulnerability intel tags column to the Vulnerabilities for IP address table on the IP address details page. These tags provide immediate insight into which vulnerabilities pose the highest threats to your organization. Previously, you had to navigate to the Vulnerabilities page to view the tags associated with a vulnerability.
Update to IP address domain details
To prevent ambiguity when RDNS and FDNS lookups resolve to the same domain for more than one IP address, we no longer show RDNS domains in the Domains for IP address table on the IP address details page.
Now, RDNS domains only appear in the IP addresses table on the IP address page and in the overview section of the IP address details page. We also removed the DNS type column from the Domains for IP address table since the table now only includes FDNS domains.
Change to dashboard widget
We removed the Next scan field from the Scan details widget on the Dashboard page because dates weren't populating correctly. In a future release, we will restore the field.
21 March 2025
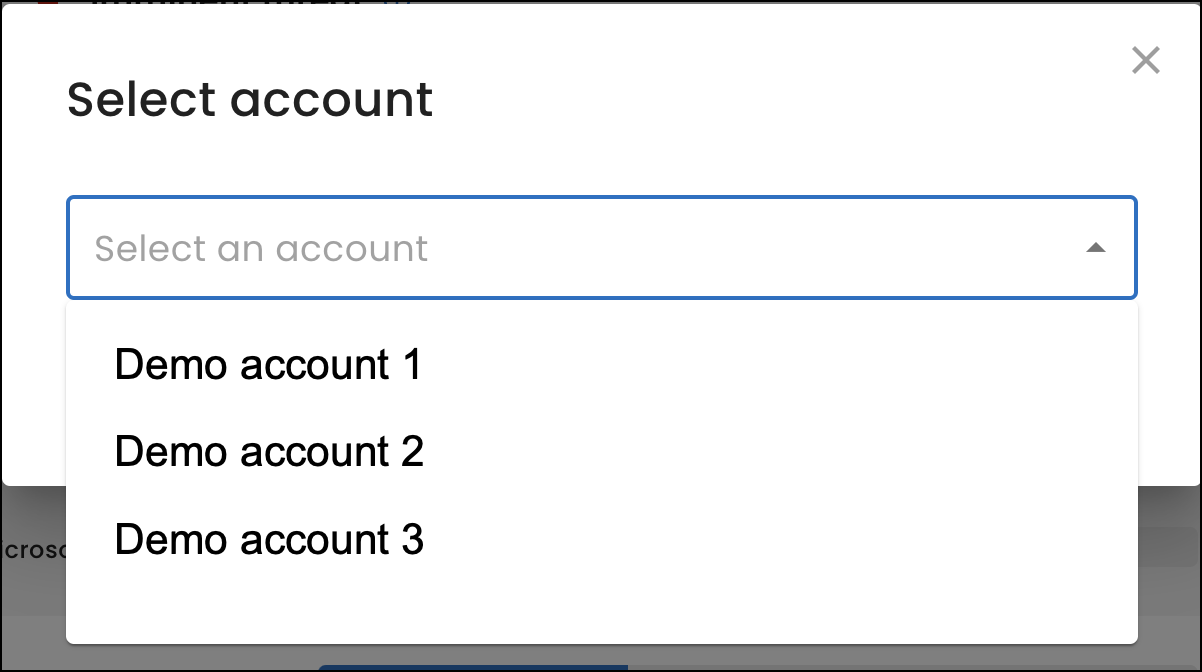
If your organization has access to multiple accounts, such as if you partner with Sixmap to offer our services to your customers, you can now select from a list of accounts after you log in.
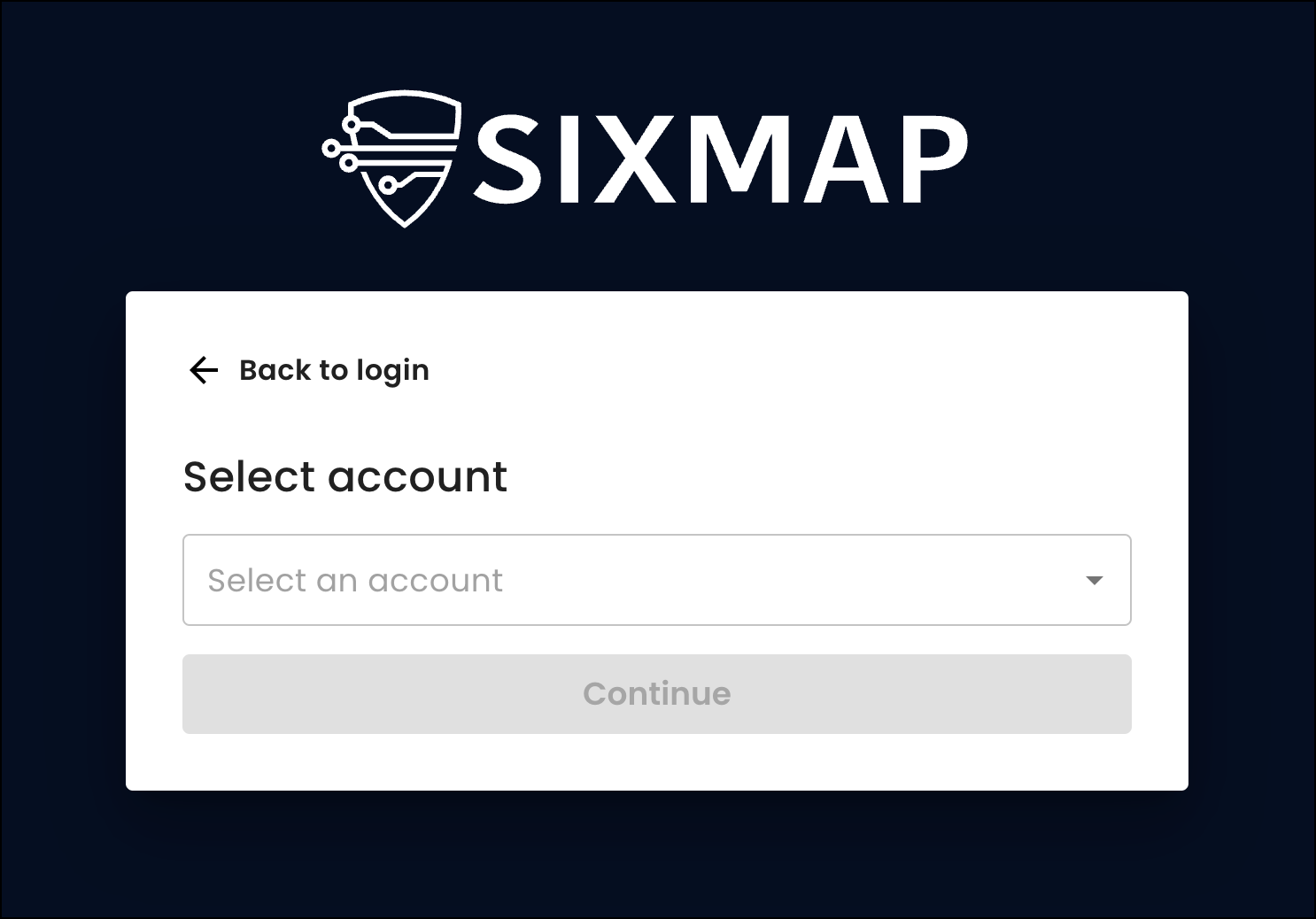
You can also change accounts from the 
18 March 2025
Enhanced authentication and authorization options
Building on the authentication upgrades we introduced in our last release, we added new authentication and authorization capabilities to give you more control over how users access your SixMap account and what they can do once logged in.
Authentication methods
We expanded the range of authentication methods available for your organization. You can now choose from these options to best suit your security and user experience needs:
- Multi-Factor Authentication (MFA): Enhance security by requiring users to provide a one-time password from an authenticator app as a second form of verification. Admins can enforce MFA for all users or allow individuals to enable it for their own accounts. For details, see MFA.
- Single Sign-On (SSO): Streamline user access by enabling SSO through your organization's identity provider. For details, see SSO.
- SCIM Provisioning: Automate user provisioning and de-provisioning through SCIM integration with your identity provider. For details, see SCIM.
Administration pages
To support these new options, we introduced new pages for admins:
-
Organization: Manage authentication settings for your organization, including enabling and disabling specific authentication methods and configuring SSO. Admins can also control how to invite and provision new users, including options for JIT (Just-In-Time) provisioning based on email domain, OAuth provider, or SSO connection.
-
Users: Manage the members of your organization who use the SixMap app. For example, you can manually invite new users, edit roles, and deactivate users. You can also manage whether a user must use multi-factor authentication (MFA), force a password reset, revoke all of a user's sessions, and edit a user's details.
-
SSO: Manage Single Sign-On (SSO) connections for your organization. SSO is an authentication method that allows users to access multiple applications and websites with a single set of login credentials.
-
SCIM: If you use SSO, manage your organization's System for Cross-domain Identity Management (SCIM) connection. SCIM automates the exchange of user identity information between your primary identity provider and SixMap.
Roles
We also introduced a new role-based access control system that enables you to use default permissions for different types of users within your organization. For more information, see Roles.
For this release, SixMap granted admin access to users selected by your organization's account representative.
User-level MFA
If your organization doesn't enforce organization-wide MFA, individual users can still enable it for their accounts through their profile settings, giving users more control over their security. For details, see MFA.
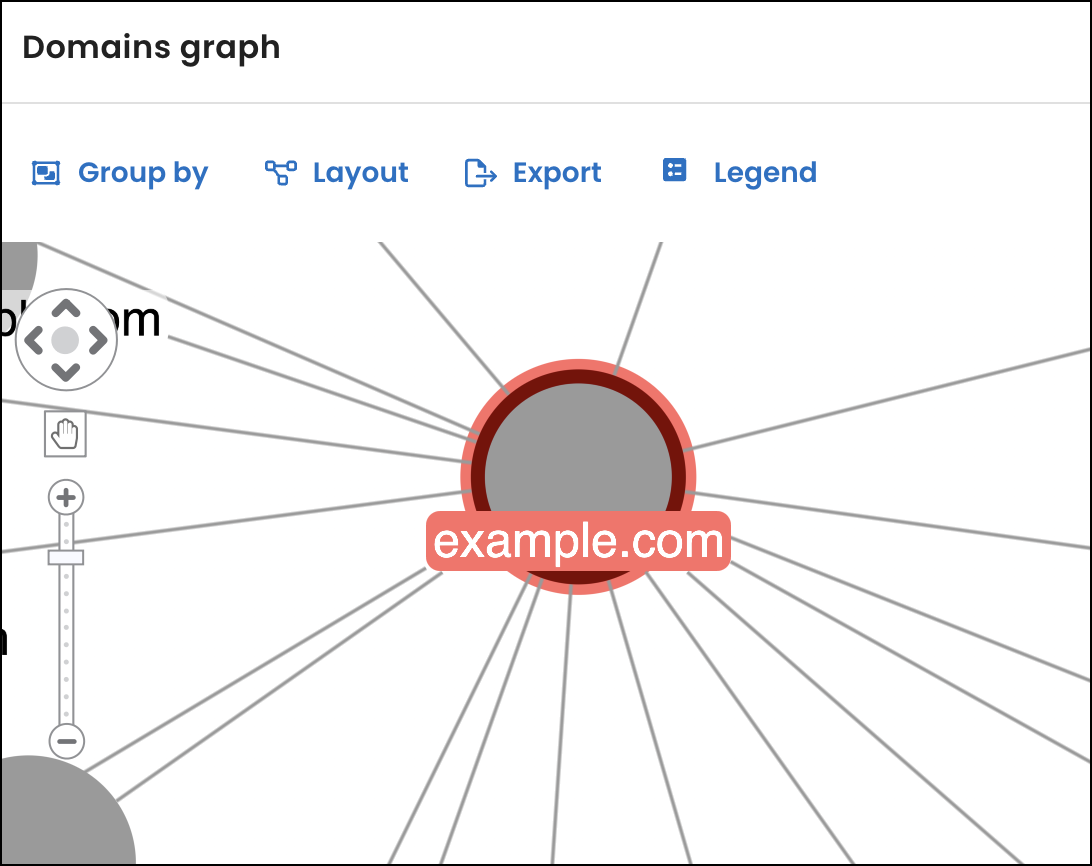
Domains graph enhancement
In response to customer feedback, we updated the Domains graph on the Attack surface page so that you can now double-click the graph nodes to open the IP addresses page. Previously, you had to double-click on the domain name to open the page.
04 March 2025
Export scan data
From the Dashboard page, under Scan history, you can now select the Export scan data (Beta) link to download a .tar.gz archive (tarball) of data from your current scan to your browser’s Downloads folder. Use the comma-separated values (CSV) files in the archive to analyze data, create reports, or integrate with other systems.
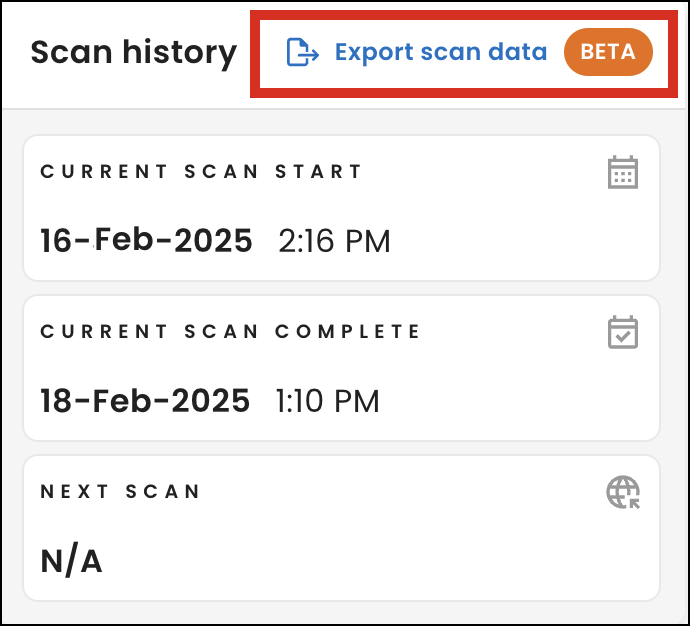
This feature is currently in beta, and due to the nature of the raw data, you may encounter minor issues or have questions about the data's structure. Please report any problems or suggestions to [email protected]. We appreciate your feedback as we refine and improve this functionality.
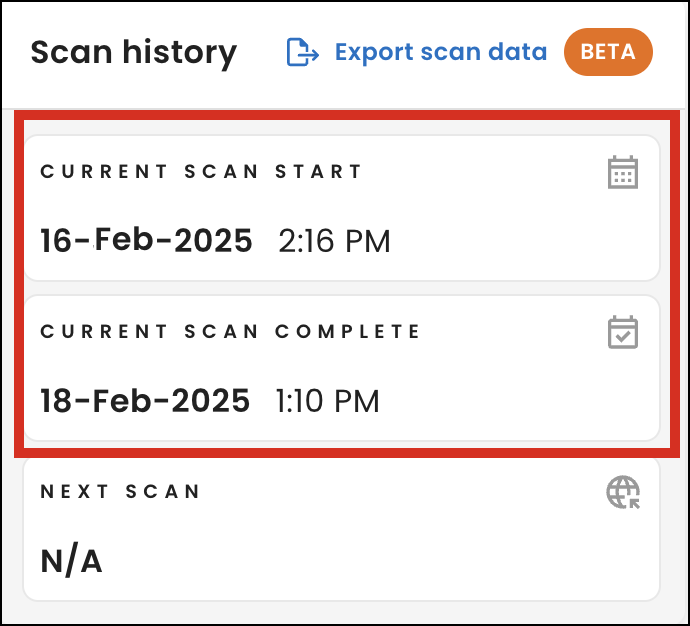
New scan date range fields
To better show the date range for when we started and completed your most recent scan, we removed the Last scan field and added the Current scan start and Current scan complete fields under Scan history on the Dashboard page.
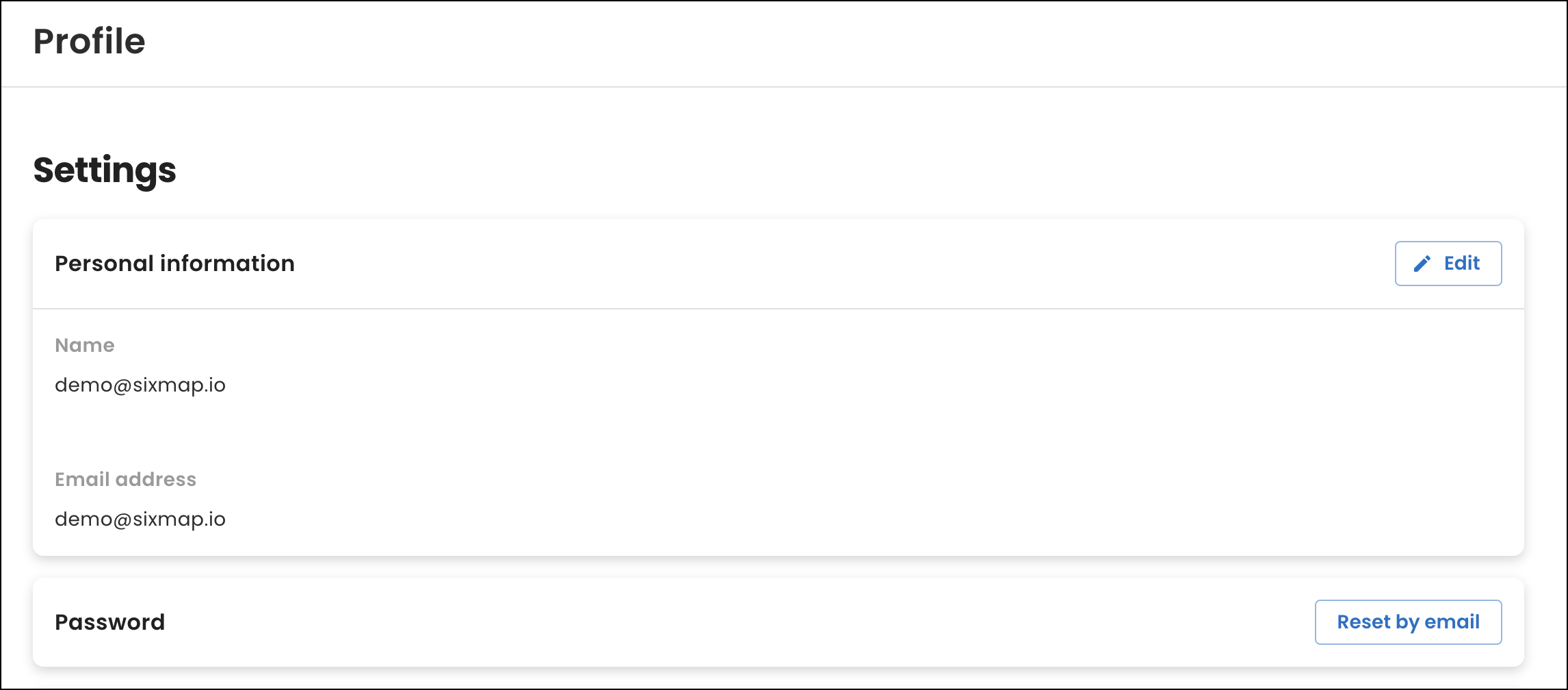
Authentication upgrades
We upgraded our authentication system to enhance account security and provide more robust authentication options. As part of the upgrade, we added a new Profile page where you can manage your personal details, including your name and password. For details about the new page, see Profile.
In an upcoming release, this upgrade will enable additional features, such as Multi-Factor Authentication (MFA) and Single Sign-On (SSO), giving you greater control and flexibility over your account security.
Users must reset their passwords to log into the SixMap app after this release. To help with this transition, we sent each user a password reset email on Tuesday, March 4, 2025. If a user did not receive the email, they can select the Sign up or reset password link from the login screen to receive the reset email.
Currently, SixMap team members add new users for your organization. In an upcoming release, organization admins will be able to add new users to the app.
18 February 2025
Dashboard and Vulnerability page improvements
To help you quickly prioritize and address urgent issues, we improved the Dashboard and Vulnerabilities pages.
On the Dashboard page, we added new widgets:
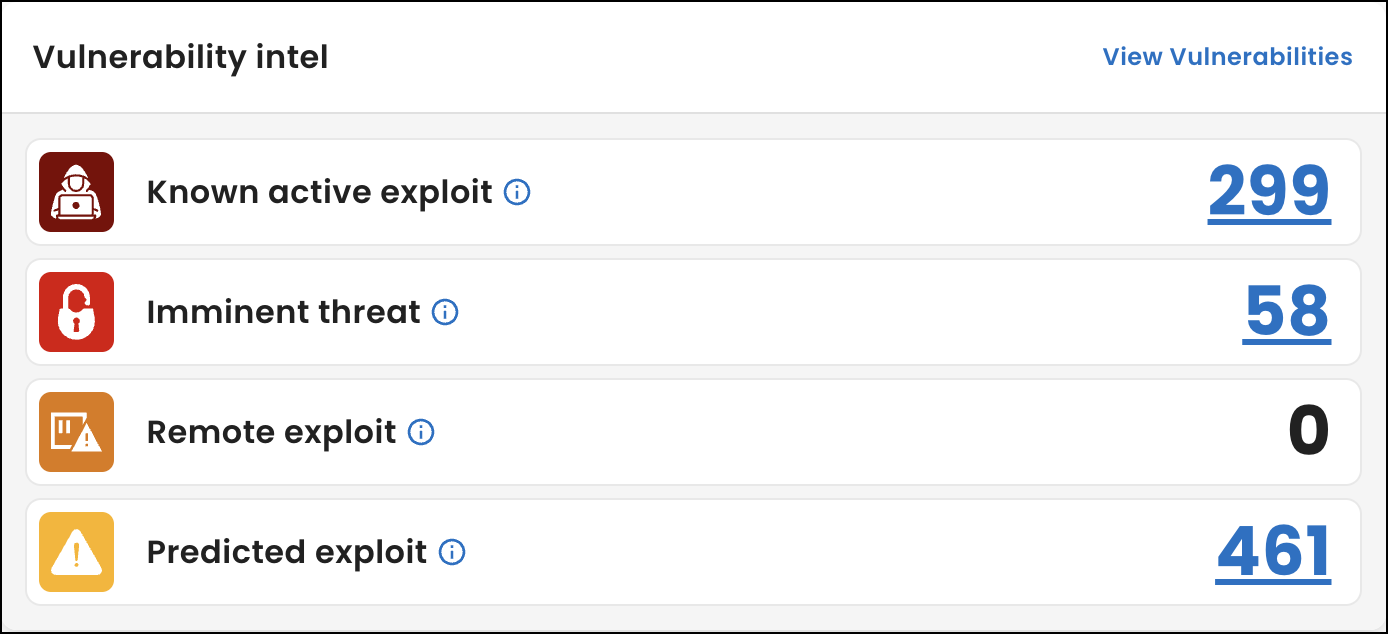
-
Vulnerability intel: Shows how many vulnerability instances have the highest threats to your organization based on tags. A tag is a label we add to scan data to help you quickly identify areas within your networks that might require attention. To assign vulnerability tags, we use industry measures such as the Known Exploited Vulnerabilities (KEV) catalog, the Exploit Prediction Scoring System (EPSS), and the Common Vulnerability Scoring System (CVSS).
For details, see Vulnerability intel.
-
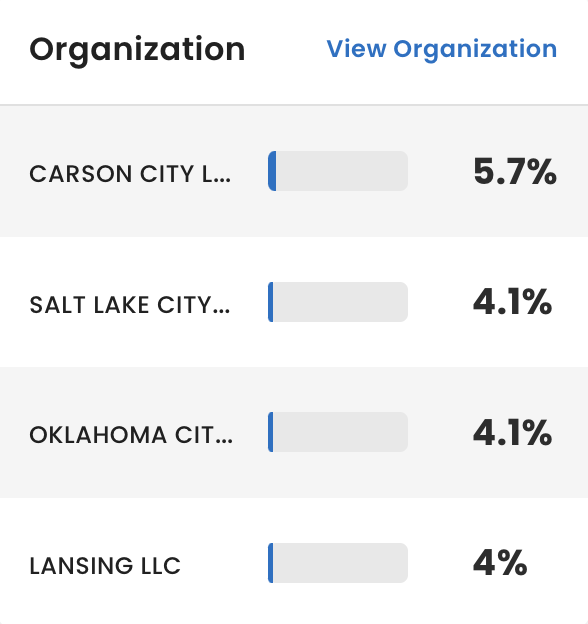
Organization: Shows the four descendant organizations from your hierarchy with the most IP addresses and the percentage of IP addresses associated with each.
For details, see Organization.
-
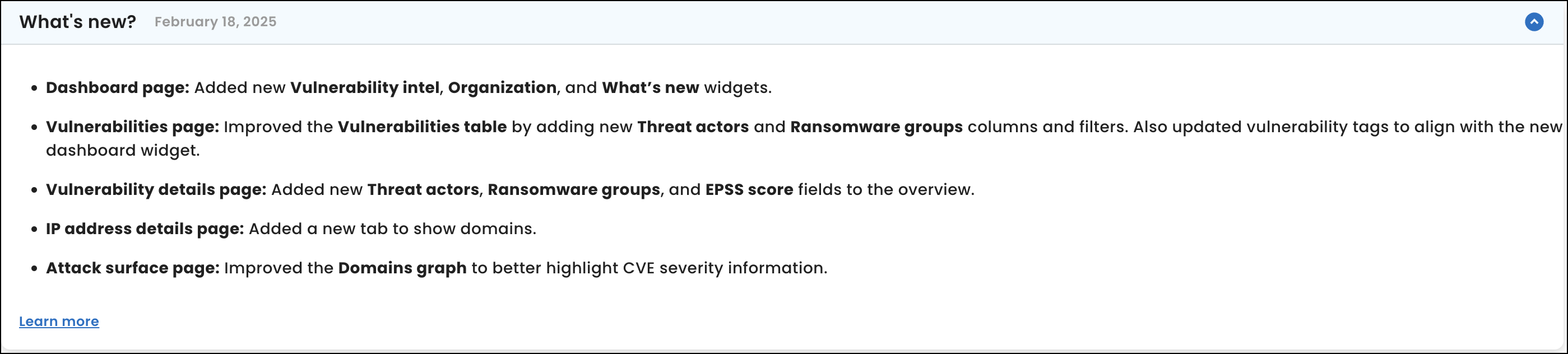
What's new: Includes highlights about the latest SixMap release.
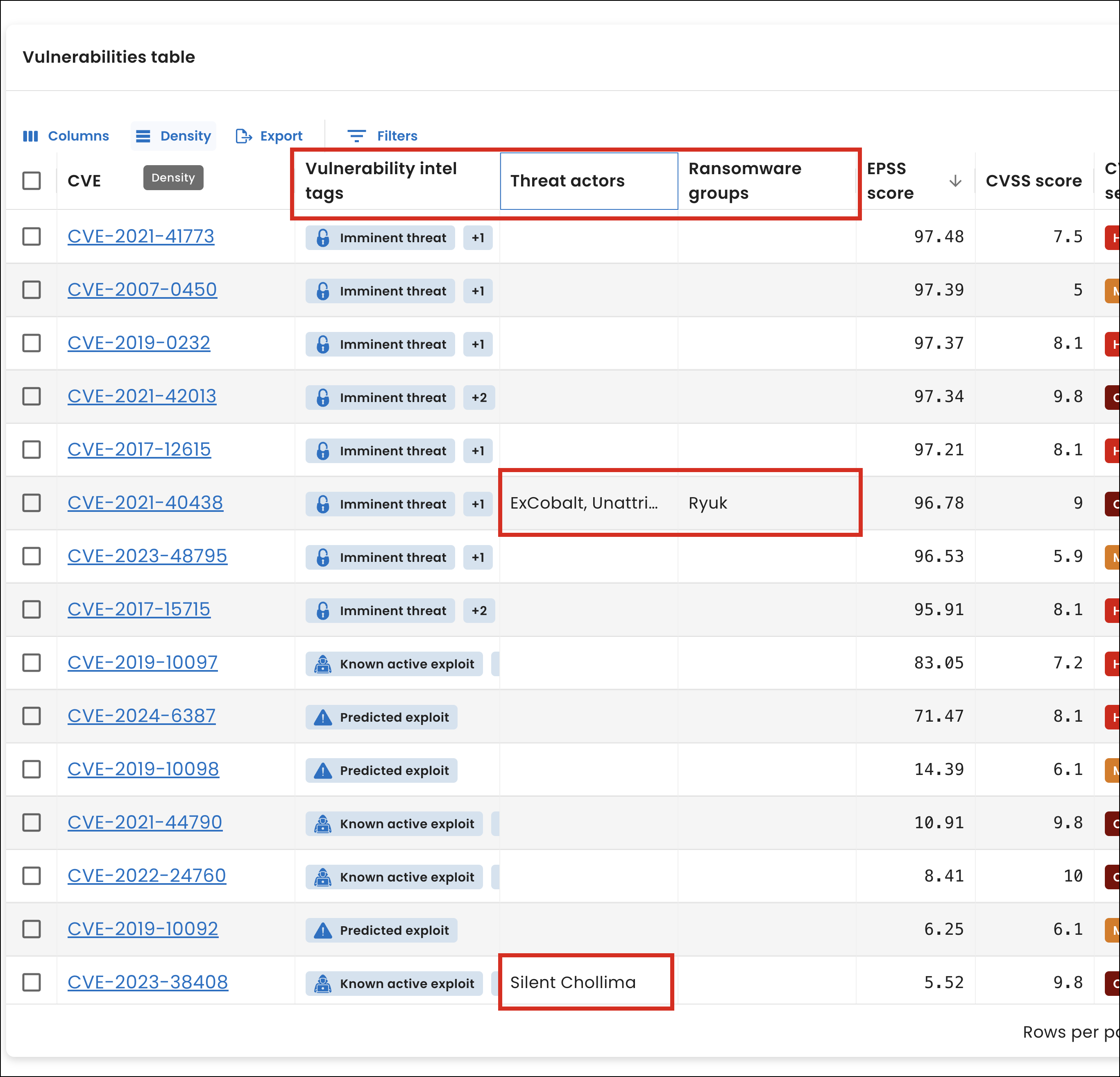
On the Vulnerabilities page, we improved the Vulnerabilities table:
-
Added new Threat actors and Ransomware groups columns to show who is associated with vulnerabilities listed in the KEV catalog. The columns are also available as filters so you can narrow the data based on whether a threat actor or ransomware group is known.
-
Changed the label of the Vulnerability tags column to Vulnerability intel tags and updated the tags to align with the Vulnerability intel widget on the Dashboard page. For details about the tag changes, see Vulnerability tag changes.
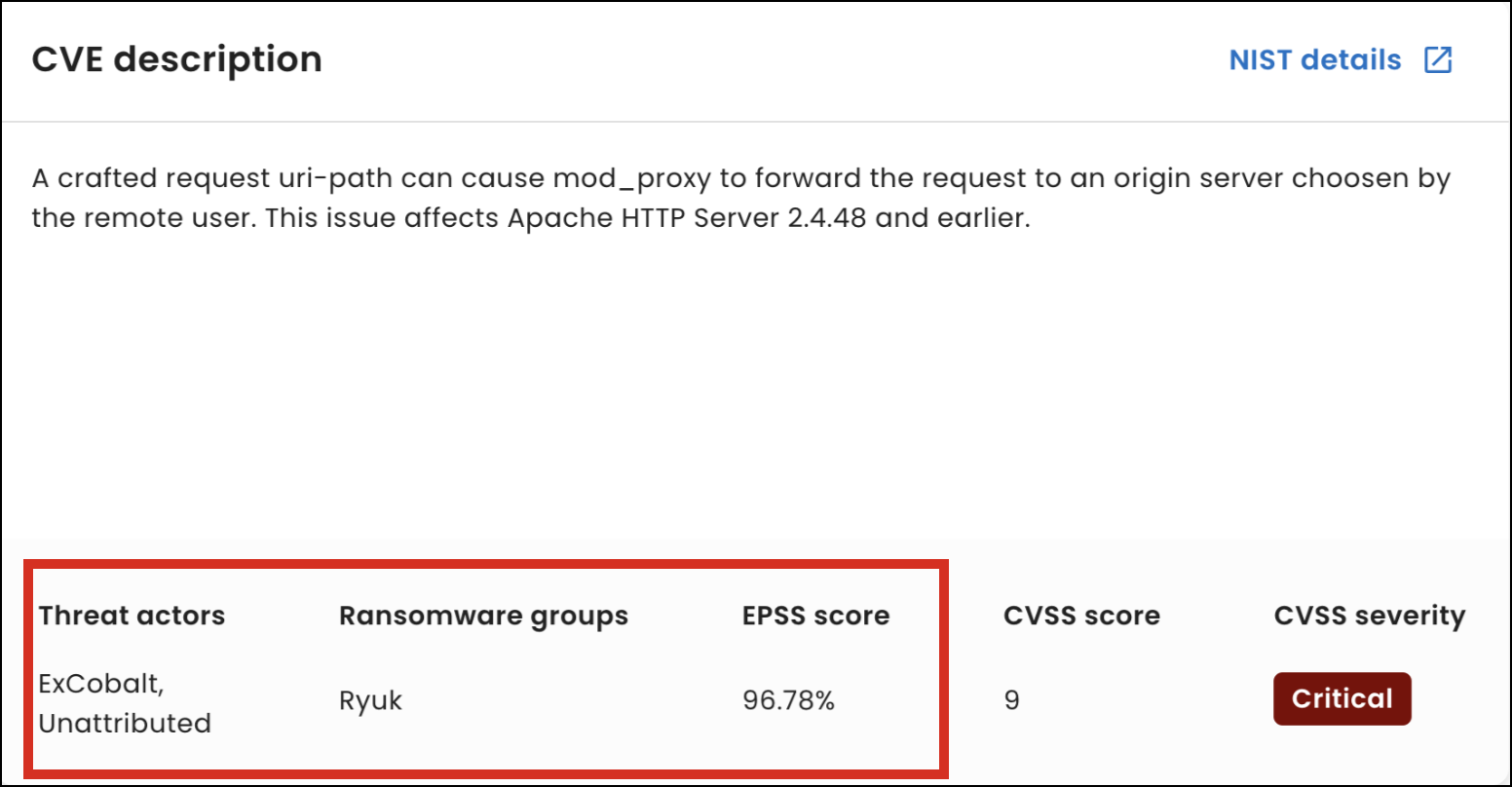
Vulnerability details page improvements
In addition to the existing description, CVSS severity, and CVSS score details in the overview section of the Vulnerability details page, you can now view threat actor, ransomware group, and EPSS score information.
To access the details page, navigate to the Vulnerabilities page and select a vulnerability from the Vulnerabilities table.
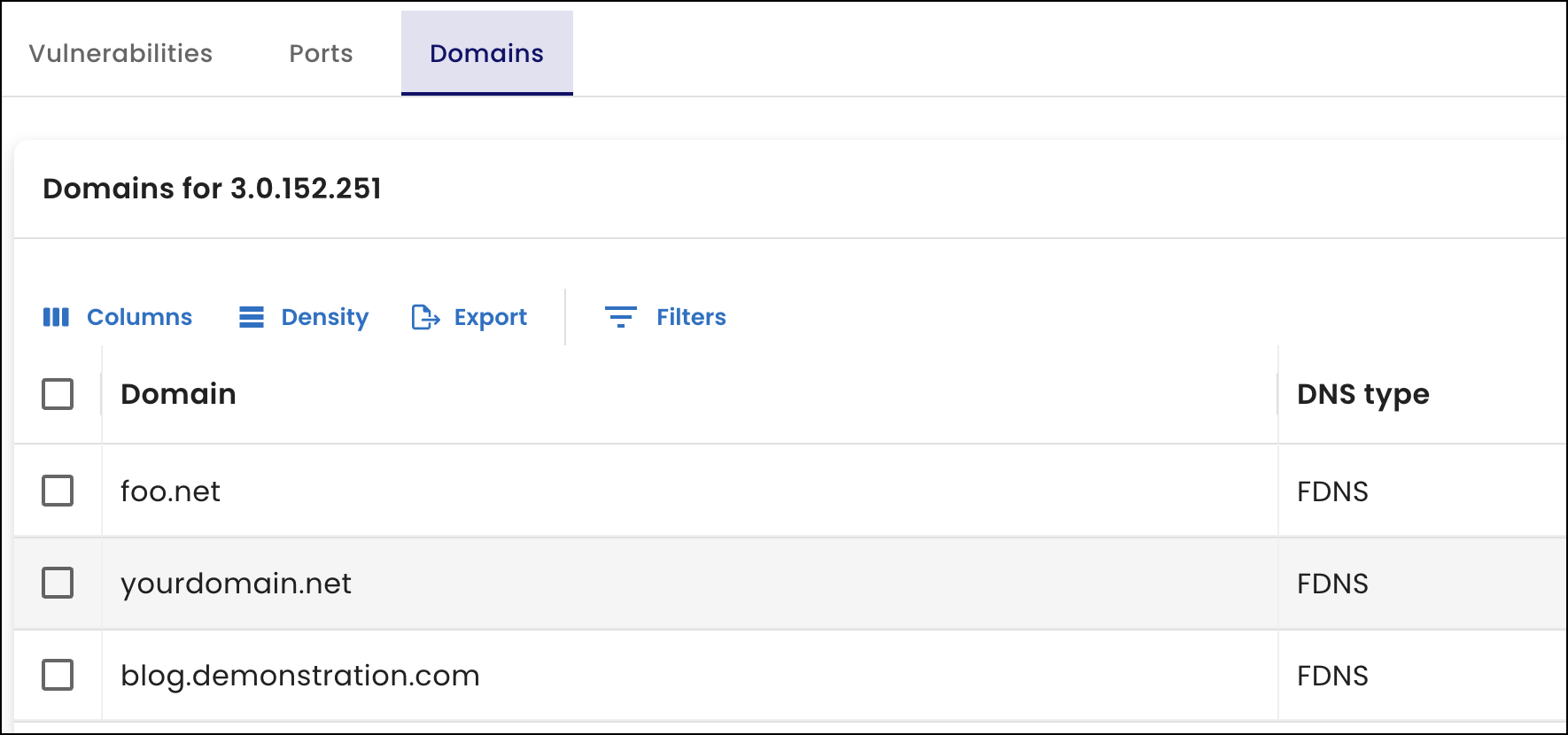
New table for IP address domains
From the IP address details page, you can now view a list of domains for an IP address and whether we matched the domain to the IP address using forward or reverse DNS lookup.
To access the new table, navigate to the IP addresses page and select an IP address from the IP addresses table. Next, select the Domains tab and view the values in the Domain and DNS type columns.
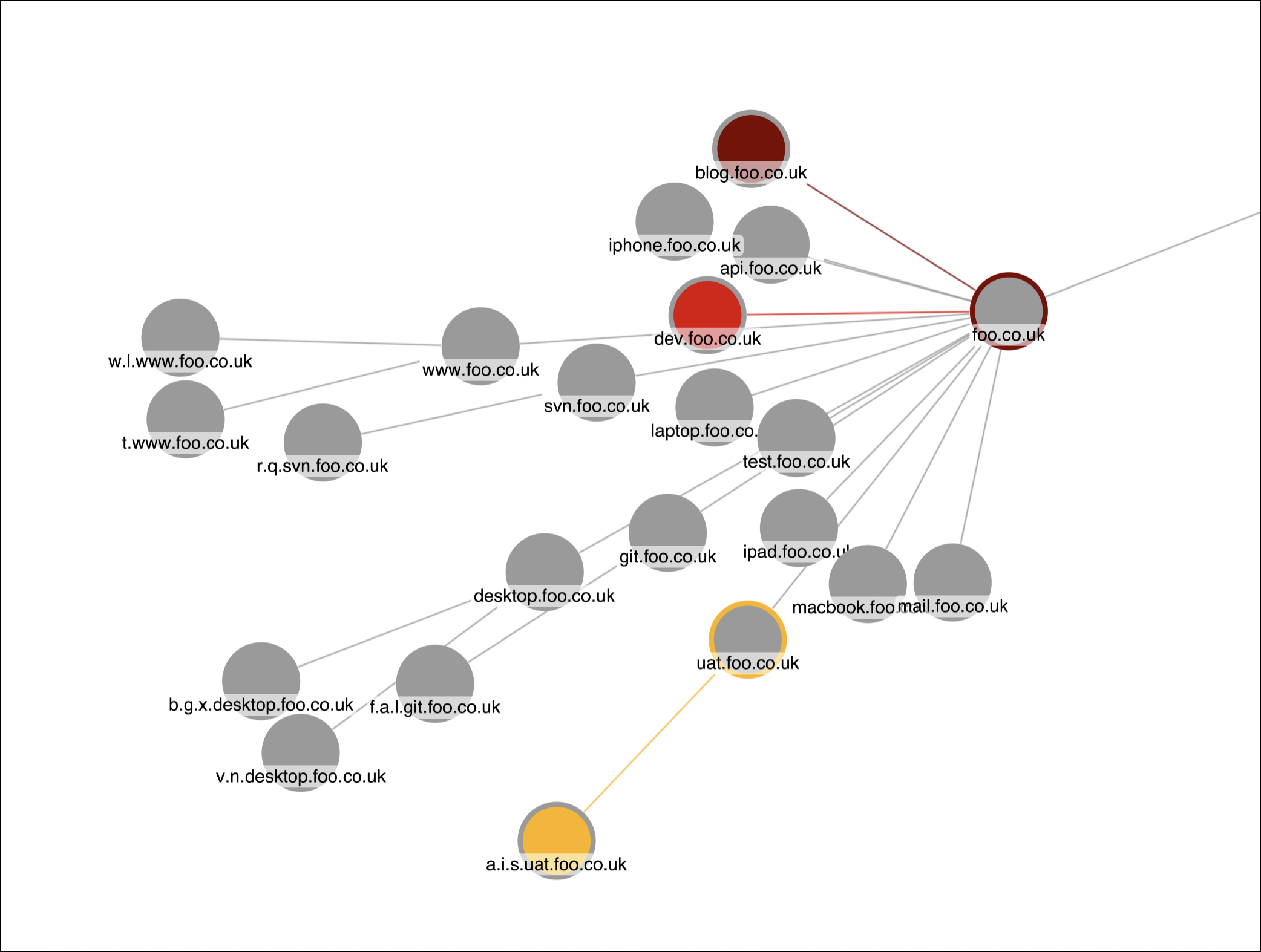
Domain graph improvements
When you view the Domains graph on the Attack surface page, you can more easily identify the Common Vulnerabilities and Exposure (CVE) levels associated with domains.
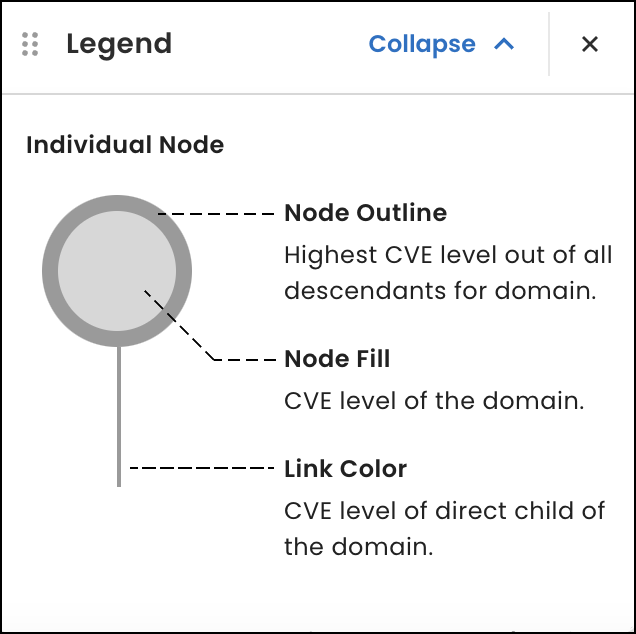
When a domain is associated with a CVE number, its node on the graph corresponds to a severity-level color. For this release, we updated the node’s outline color to indicate the highest CVE level found for the domain out of all its descendants. Also, the color of the line linking the node to another node now indicates the CVE level of the domain’s direct child.
To help you understand the changes, we also added a legend to the graph.
28 January 2025
This release includes the following:
Organization filters
To help you generate customized views and reports tailored to individual organizational units — enabling faster, more informed decisions, prioritization of critical vulnerabilities, and actionable insights relevant to specific needs and responsibilities — we added a new Organization filter to tables throughout the SixMap app.
From the table you’re using to create a custom view, select Filters, then choose Organization under Columns. Next, search for or select an organization from the organization list that appears.
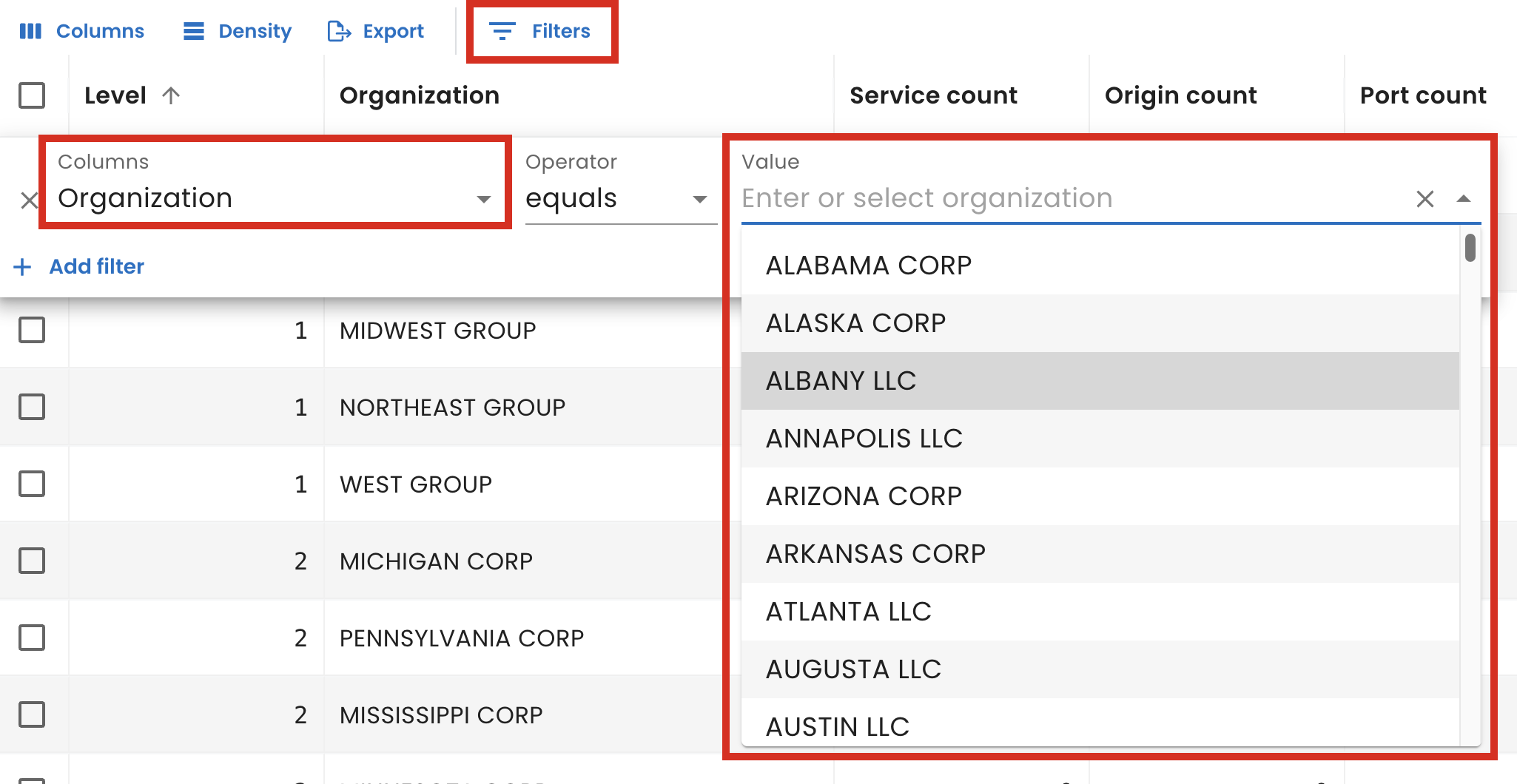
To filter by more than one organization or to further narrow the data in the table, select Add filter and select the additional criteria.
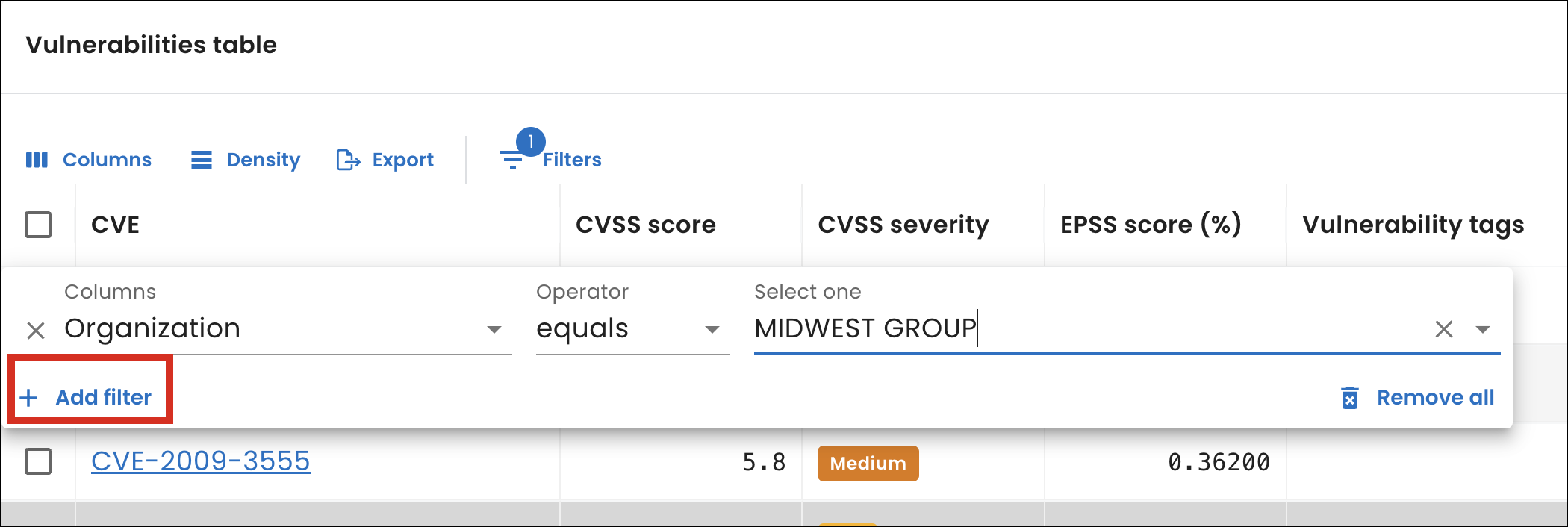
For a list of tables with the new filter, see Organization filter.
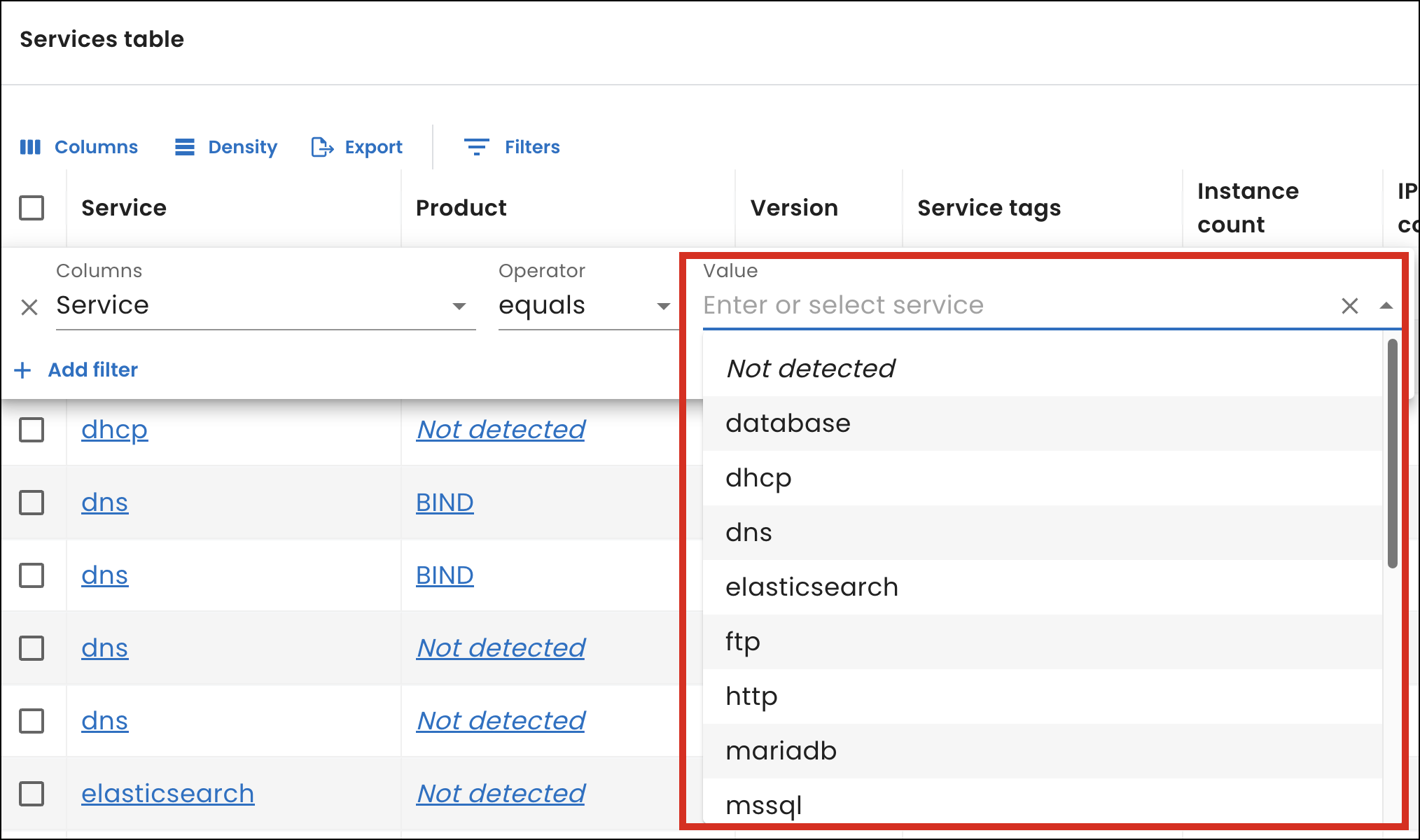
Identify shadow IT
Shadow IT is unofficial, user-installed software that operates outside the control of the IT department. This unmonitored software can create security and compliance issues, which makes maintaining an accurate overview of your systems difficult.
To help identify shadow IT, you can now view a list of unique services we identified from your most recent scan when you filter by service from the Services table on the Services page. Previously, you had to manually enter the name of a service to filter for it.
Vulnerability table order
Based on customer feedback, the Vulnerabilities table on the Vulnerabilities page now sorts vulnerabilities from highest to lowest by the Exploit Prediction Scoring System (EPSS) score, making it easier to prioritize the most critical vulnerabilities. Previously, the table sorted vulnerabilities by CVE numbers, from oldest to most recent.