CVE program
The Common Vulnerabilities and Exposure (CVE) program helps information technology and cybersecurity professionals track cybersecurity flaws in their services. Participating groups called CVE Numbering Authorities (CNAs) identify, define, and catalog vulnerabilities and publish their records. The groups include security companies, research organizations, and major IT companies such as IBM and Cisco. Through this program, organizations can communicate consistent descriptions of vulnerabilities and coordinate efforts to address them.
The MITRE Corporation manages the numbering system with funding from the Cybersecurity and Infrastructure Security Agency (CISA), part of the U.S. Department of Homeland Security.
How the CVE program works
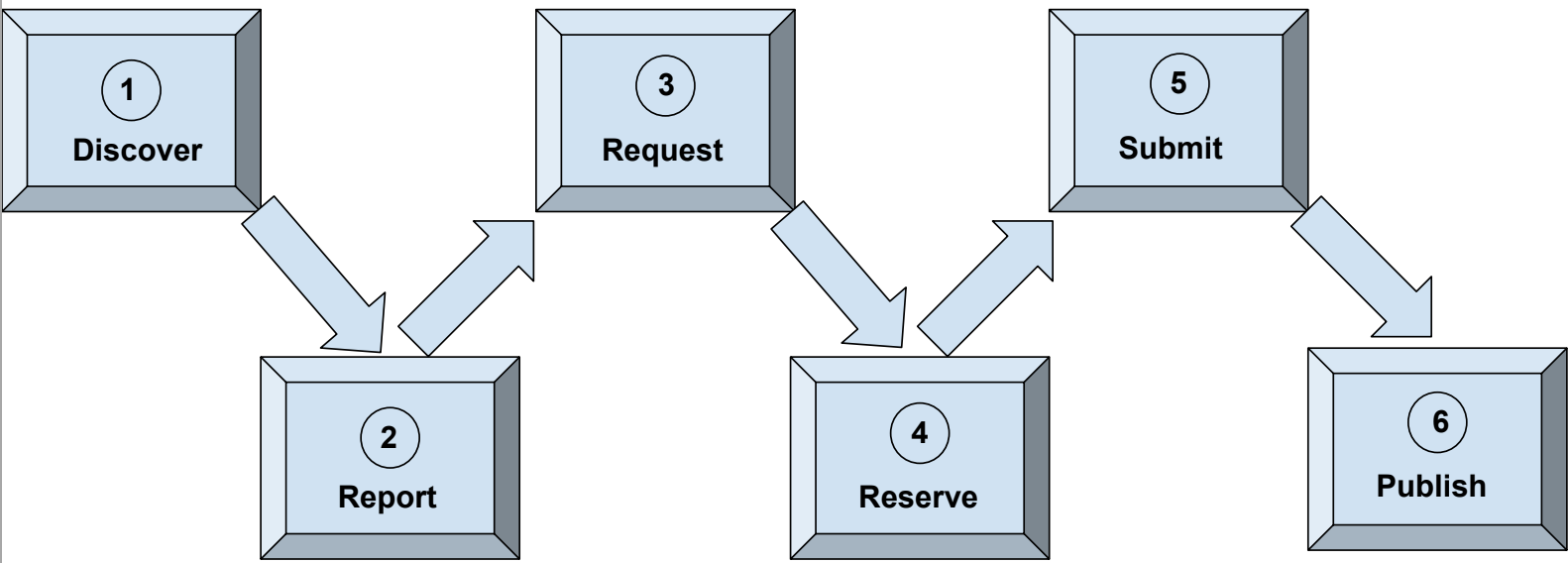
First, a person or organization discovers a vulnerability and reports it to the CVE program through a CNA. The CNA then requests a CVE ID for the vulnerability and reserves the number so stakeholders can coordinate and manage its details. Next, the CNA confirms the vulnerability, submits details about it to a CVE record, and then publishes the record to the CVE list so that the public can view and download the details.
Common Vulnerability Scoring System (CVSS)
After a CNA publishes a vulnerability to the CVE list, it appears in the National Vulnerability Database (NVD), which the U.S. National Institute of Standards and Technology, part of the U.S. Department of Commerce, maintains. From the NVD, analysts use the Common Vulnerability Scoring System (CVSS) to assess the severity of the vulnerability and assign a score to it. The score they report in the database is typically the CVSS Base Score, which measures vulnerability characteristics that don't change over time.
CVSS scores also consist of other metrics that show how vulnerabilities change, such as when software vendors, organizations, or threat actors take actions.
To calculate the base score, analysts use a formula consisting of metrics measuring the ease and impact of exploiting a vulnerability. For each vulnerability SixMap identifies for your organization, you can view a graph that displays whether the impact from specific metrics would be high, low, or none. For details, see Vulnerability details.
Organizations then use the following score ranges to prioritize how they manage their vulnerabilities:
| Severity | Range |
|---|---|
| Low | 0.1-3.9 |
| Medium | 4.0-6.9 |
| High | 7.0-8.9 |
| Critical | 9.0-10.0 |
For comprehensive details about the program, see the documentation at FIRST.org.
Exploit Prediction Scoring System (EPSS)
Another measure to help prioritize vulnerability management is the Exploit Prediction Scoring System (EPSS). The EPSS calculates a probability score to estimate threat actors' likelihood of exploiting a vulnerability.
To calculate scores, the EPSS model analyzes data from other systems, such as the CVE list, CVSS metrics, and government websites, and compares scores against each other to show how the vulnerability ranks among all current vulnerabilities. The combination of probability and ranking helps organizations determine which vulnerabilities to address first.
The EPSS score, ranging from 0 to 1 (0 to 100% exploitation chances), estimates the probability that a threat actor will exploit a vulnerability within the next 30 days. This real-time insight allows organizations to stay ahead of potential threats.
For comprehensive details about the system, see the documentation at FIRST.org.
Known Exploited Vulnerabilities (KEV)
Information technology and cybersecurity professionals can also use CISA's Known Exploited Vulnerabilities (KEV) catalog to track and manage vulnerabilities. The catalog is the U.S. government's authoritative source of vulnerabilities that threat actors have already used.