Vulnerability instances
A vulnerability is a cybersecurity flaw associated with a Common Vulnerabilities and Exposures (CVE) number.
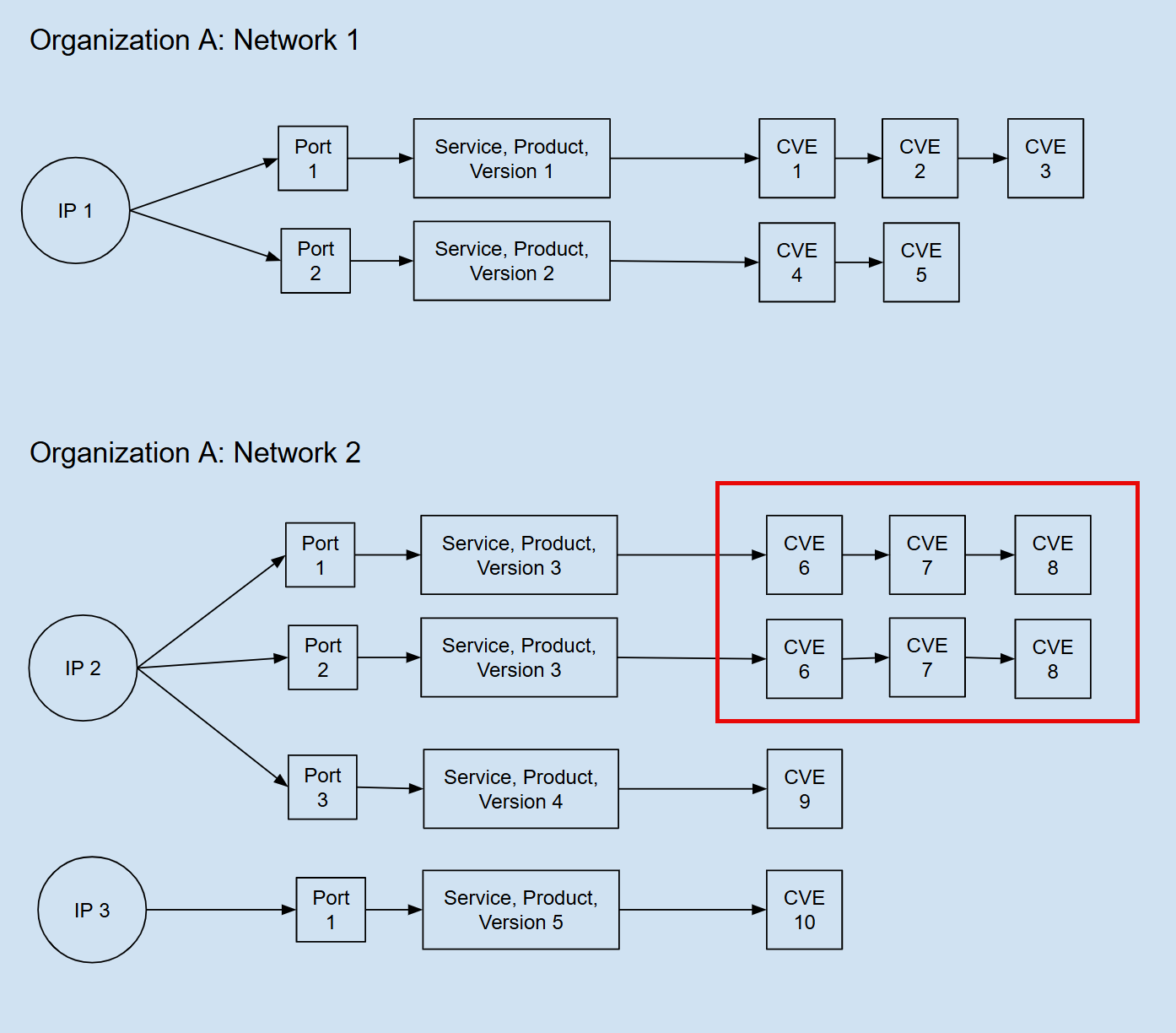
To determine the number of vulnerability instances for a data set, we count the CVEs identified for a service, product, and version combination that an IP address runs on an open port. If an IP address runs the combination on multiple ports, we count the vulnerabilities for each port as additional instances.
For example, in the figure below, we count six vulnerabilities for Service, Product, Version 3 because it runs on two ports.
Vulnerability instance counts in tables
We show the vulnerability count associated with different views of your organization’s data in tables throughout the SixMap app.
For example:
-
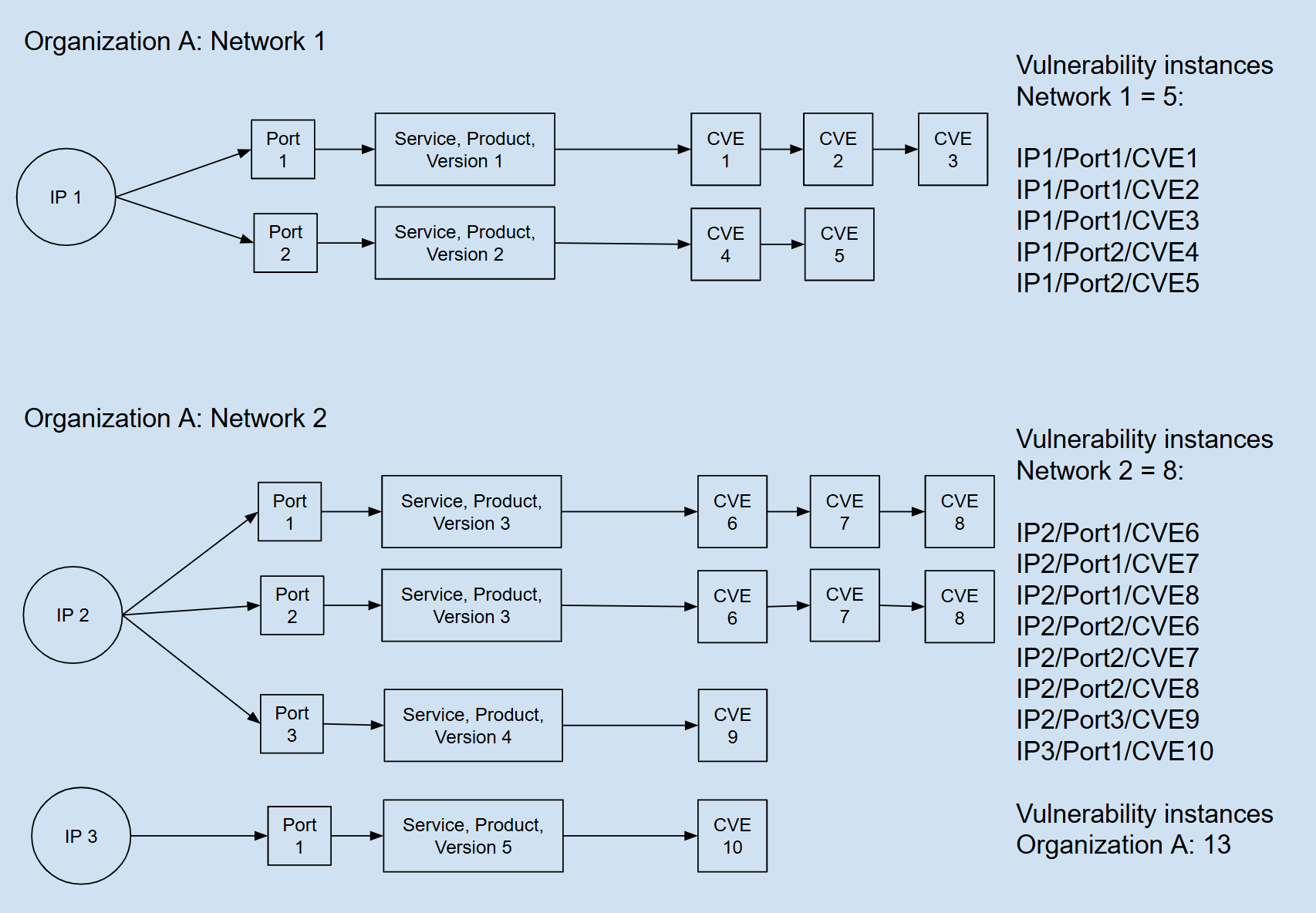
On the Organization page, each row in the Hierarchy table represents an organization, so the count shows the number of vulnerabilities across all of the organization’s IP addresses.
In the figure below, the vulnerability instance count for Organization A is 13. Three IP addresses run five product, service, and version combinations associated with ten vulnerabilities across six ports.
-
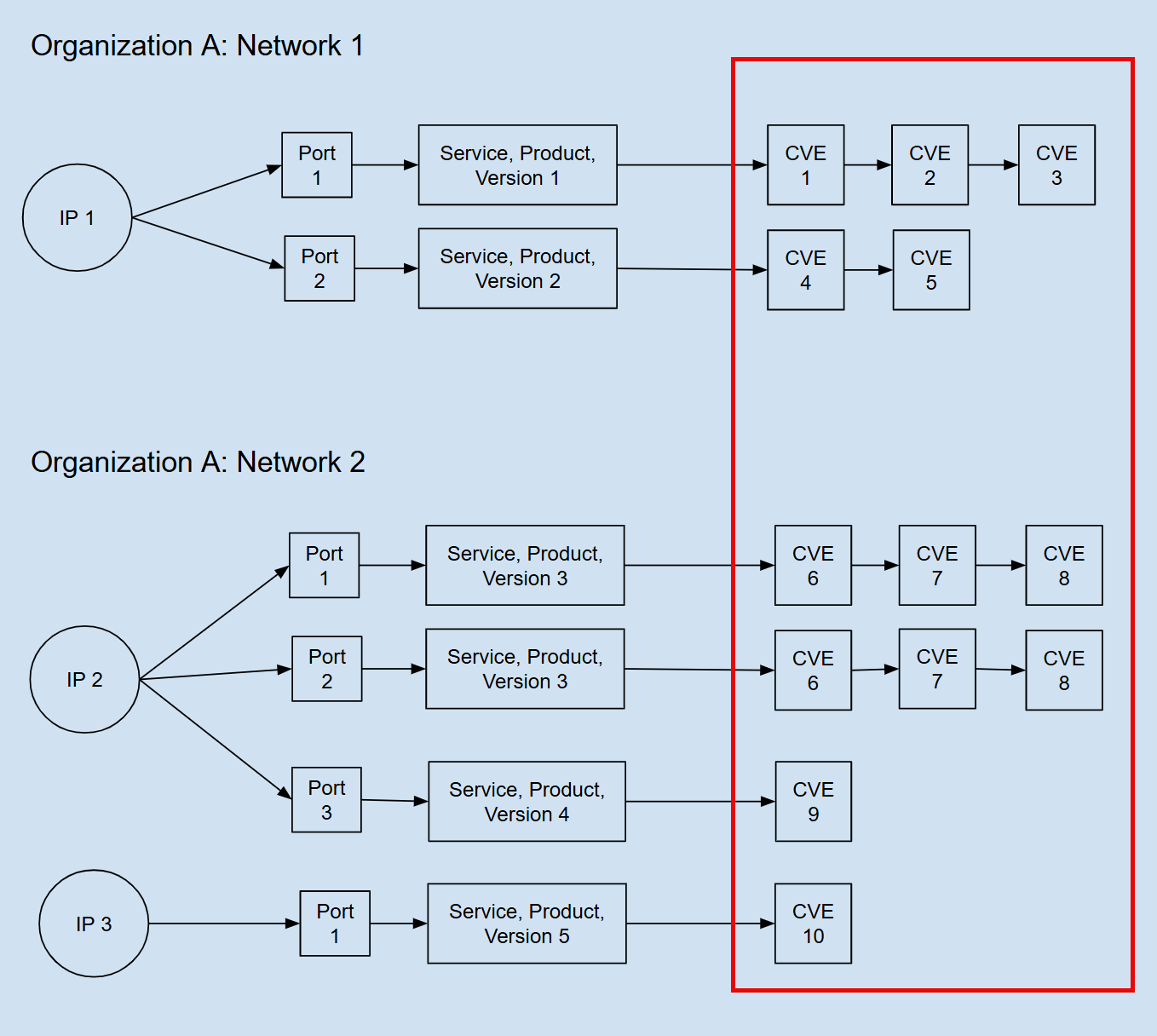
On the Networks page, each row in the Networks table represents a range of IP addresses, so the count represents the number of vulnerabilities across all the IP addresses in the range.
In the figure below, the vulnerability instance count for Network 2 is eight. Two IP addresses run three service, product, and version combinations associated with five vulnerabilities across four ports.
-
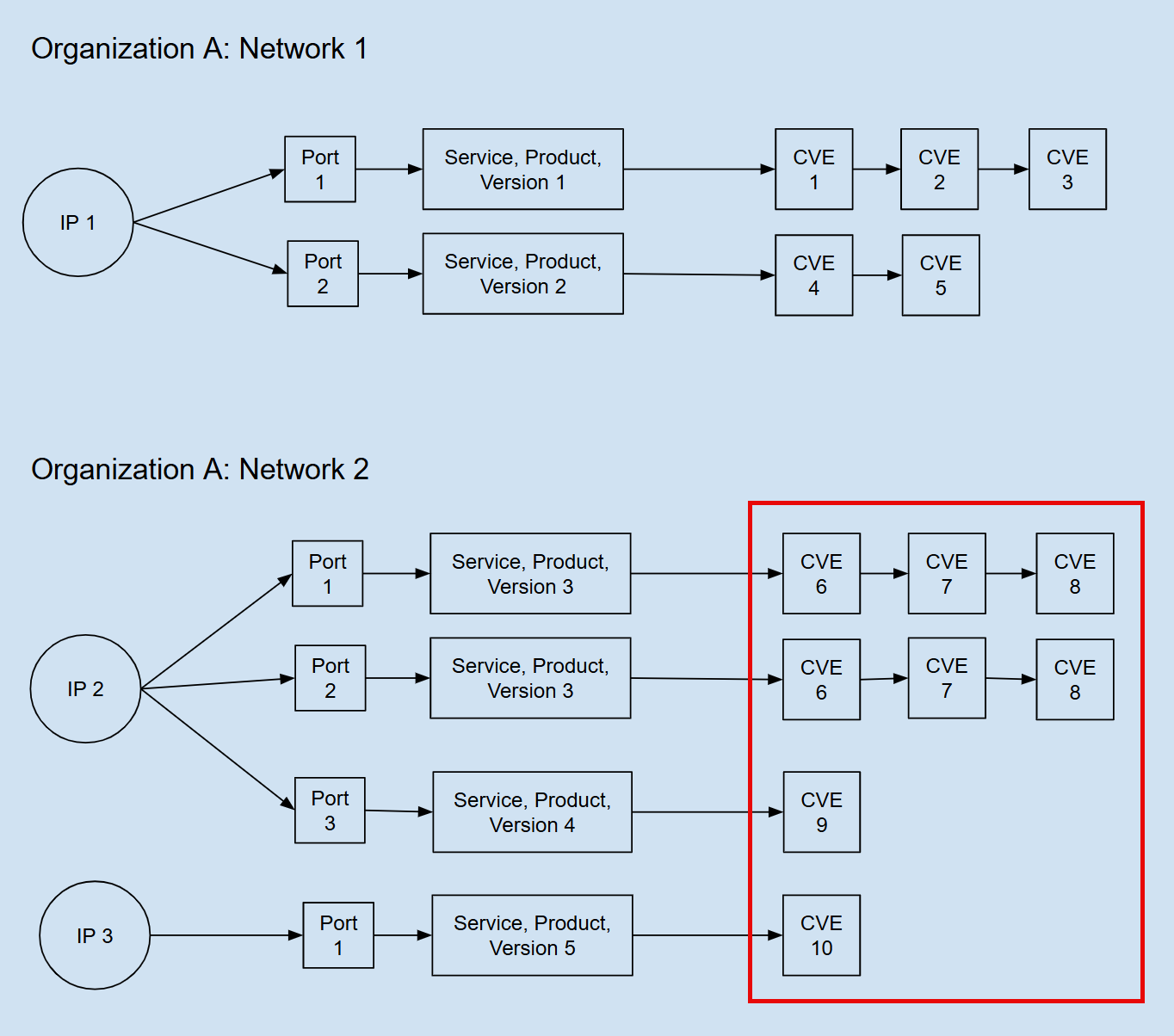
On the Services page, each row in the Services table represents a service, product, and version combination, so the count shows the number of vulnerabilities across each IP address running the combination on a port.
In the figure below, the vulnerability instance count for Service, Product, Version 3 is six because there are three vulnerabilities, and one IP address runs the combination on two ports.